
Let's talk about one search engine used by pentesters / hackers - Google, more precisely about the hidden capabilities of Google.
Google dorks
What is Google Dorks?
Google Dork or Google Dork Queries (GDQ) is a set of queries to identify the grossest security holes. Anything that is not properly hidden from search engines.
For brevity, such requests are called Google Dorks, or simply Dorks, like those admins whose resources were hacked using GDQ.
Google operators
To begin with, I would like to provide a small list of useful Google commands. Among all the commands for advanced Google search, we are mainly interested in these four:
site - search for a specific site;
inurl - indicate that the search words should be part of the page / site address;
intitle - search operator in the title of the pages themselves;
ext or filetype - search for files of a specific type by extension.
Also, when creating a Dork, you need to know several important operators, which are set by special characters.
| - OR operator, or vertical slash (logical or) indicates that you need to display results containing at least one of the words listed in the query.
"" - the quotation mark operator indicates an exact match.
- - the minus operator is used to exclude from the output results with the words specified after the minus.
* - operator asterisk, or asterisk is used as a mask and means "anything".
Where to find Google Doors
The most interesting dorks are fresh, and the freshest are those that the pen tester found himself. However, if you get too carried away with experiments, you will be banned from Google ... until you enter the captcha.
If you don't have enough imagination, you can try to find fresh dorks on the net. The best site for finding dorks is Exploit-DB.
Exploit-DB online service is a non-profit project of Offensive Security. If anyone is not in the know, this company is engaged in training in the field of information security, and also provides pentesting (penetration testing) services.
The Exploit-DB database contains a huge number of dorks and vulnerabilities. To search for dorks, go to exploit-db.com and go to the Google Hacking Database tab.

The base is updated daily. At the top you can find the latest additions. On the left side is the date of adding the dork, title and category. At the bottom, you will find the tracks sorted by category.
Another good site is google-dorking.com. There you can often find interesting, new dorks that do not always end up on Exploit-DB.
Google Dorks use cases
Here are some examples of dorks. When experimenting with dorks, don't forget the disclaimer!
This material is for informational purposes only. It is addressed to professionals in the field of information security and those who are going to become one. The information presented in the article is provided for informational purposes only. Neither the editors of the site www.spy-soft.net nor the author of the publication bear any responsibility for any harm caused by the material of this article.
Roads for finding site problems
Sometimes it is useful to examine the structure of a site by getting a list of files on it. If the site is made on the WordPress engine, then the repair.php file stores the names of other PHP scripts.
The inurl tag tells Google to search for the first word in the link body. If we wrote allinurl, then the search would occur throughout the body of the link, and the search results would be more cluttered. Therefore, it is enough to make a request like this:
inurl: /maint/repair.php? repair = 1
As a result, you will receive a list of WP sites, whose structure can be viewed through repair.php.
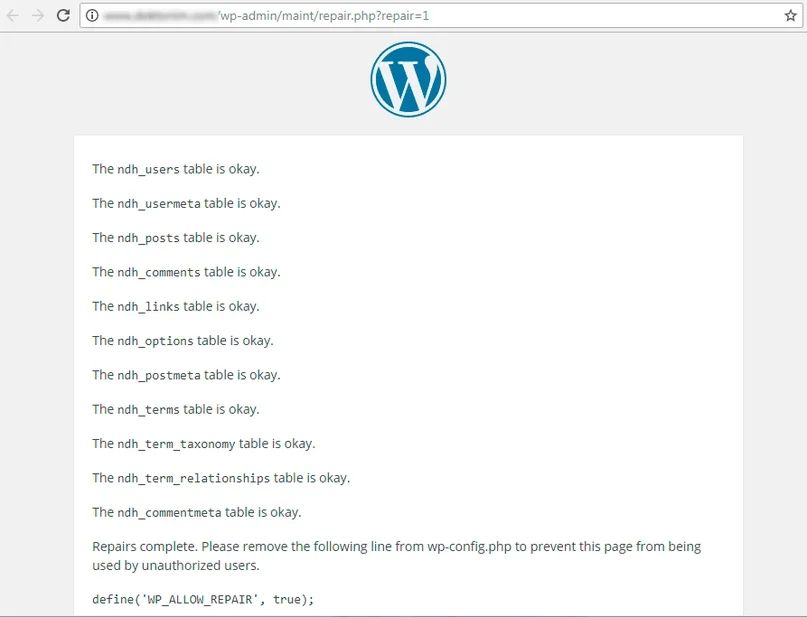
Examining the structure of a WP site
A lot of problems for administrators are delivered by WordPress with unnoticed configuration errors. From the open log you can find out at least the names of scripts and downloaded files.
inurl: "wp-content / uploads / file-manager / log.txt"
In our experiment, the simplest request allowed us to find a direct link to the backup in the log and download it.
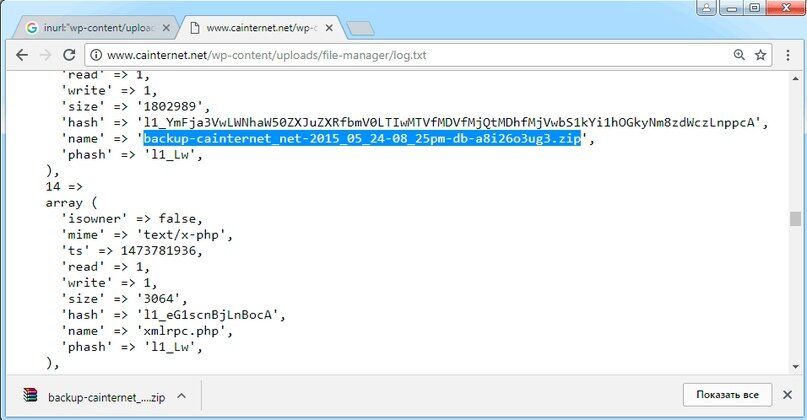
Finding valuable info in WP logs
A lot of valuable information can be extracted from the logs. It is enough to know how they look and how they differ from the mass of other files. For example, an open source database interface called pgAdmin creates a service file pgadmin.log. It often contains usernames, database column names, internal addresses, and the like.
The log is found by an elementary request:
ext: log inurl: "/ pgadmin"
There is an opinion that open source is safe code. However, in itself, the openness of the source means only the opportunity to research them, and the goals of such research are far from always good.
For example, Symfony Standard Edition is popular among web application development frameworks. When deployed, it automatically creates a parameters.yml file in the / app / config / directory, where it stores the name of the database, as well as the login and password.
You can find this file with the following query:
inurl: app / config / intext: parameters.yml intitle: index.of

Another file with passwords
Of course, then the password could be changed, but most often it remains the same as it was set at the stage of deployment.
The open source UniFi API browser tool is increasingly used in the corporate environment. It is used to manage segments of wireless networks created according to the principle of "seamless Wi-Fi". That is, in an enterprise network deployment scheme in which multiple access points are controlled from a single controller.
The utility is designed to display data requested through Ubiquiti's UniFi Controller API. With its help, it is easy to view statistics, information about connected clients and other information about the operation of the server through the UniFi API.
The developer honestly warns: “Please do keep in mind this tool exposes A LOT OF the information available in your controller, so you should somehow restrict access to it! There are no security controls built into the tool ... ". But many do not seem to take these warnings seriously.
Knowing about this feature and asking one more specific request, you will see a lot of service data, including application keys and passphrases.
inurl: "/ api / index.php" intitle: UniFi
General search rule: first, we define the most specific words that characterize the selected target. If it's a log file, what makes it different from other logs? If it is a file with passwords, where and in what form can they be stored? Bullet words are always found in some specific place - for example, in the header of a web page or its address. By limiting the scope of your search and setting precise markers, you will get raw search results. Then clean it of debris by specifying the request.
Open NAS search paths
Home and office network storages are popular these days. Many external drives and routers support the NAS function. Most of their owners do not bother with protection and do not even change default passwords like admin / admin. You can find popular NAS by the typical titles of their web pages. For example, the request:
intitle: "Welcome to QNAP Turbo NAS"
will display a list of QNAP NAS IPs. All that remains is to find a weakly protected one among them.
inurl: share.cgi? ssid =
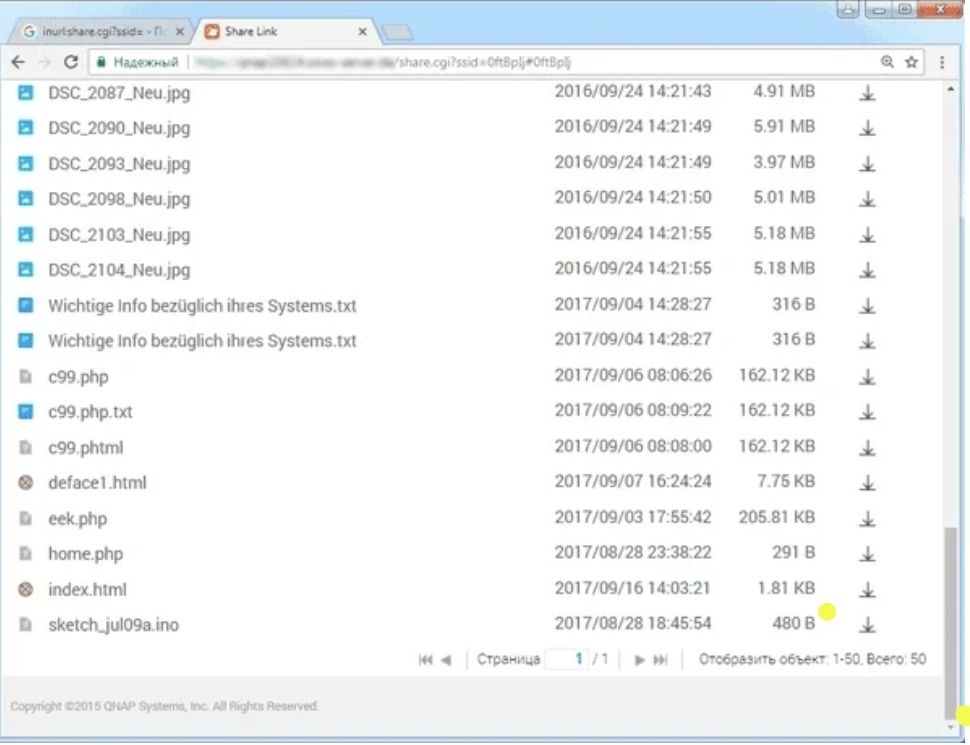
Finding shared files
The QNAP cloud service (like many others) has the function of sharing files through a closed link. The problem is, it’s not that private.
This simple query shows files shared through the QNAP cloud. They can be viewed directly from the browser or downloaded for more detailed information.
Dorks for searching IP cameras, media servers and web admin codes
In addition to NAS, advanced Google searches can find tons of other web-based network devices.
CGI scripting is most commonly used for this, so the main.cgi file is a promising target. However, he can meet anywhere, so it is better to clarify the request.
For example, adding a typical call to it? Next_file. As a result, we get a dork of the form:
inurl: "img / main.cgi? next_file"
In addition to cameras, there are media servers in a similar way, open to everyone. This is especially true for Twonky servers manufactured by Lynx Technology. They have a very recognizable name and default port 9000.
For cleaner search results, it is better to include the port number in the URL and exclude it from the text portion of web pages. The request takes the form
intitle: "twonky server" inurl: "9000" -intext: "9000"
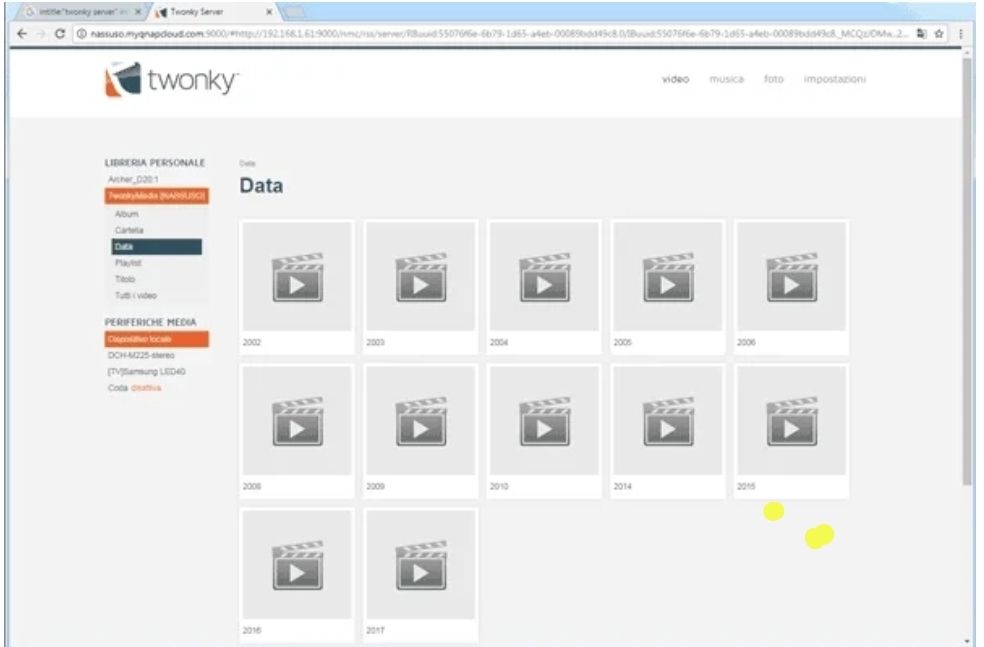
Video library by years
Typically a Twonky server is a huge media library sharing content via UPnP. Authorization for them is often disabled "for convenience".
Roads for finding vulnerabilities
Big data is all the rage right now, and it is believed that adding Big Data to anything will magically work better. In reality, there are very few real specialists on this topic, and with the default configuration, big data leads to large vulnerabilities.
Hadoop is one of the simplest ways to compromise tera and even petabytes of data. This open source platform contains well-known headers, port numbers, and service pages that make it easy to find the nodes it controls.
intitle: "Namenode information" AND inurl: ": 50070 / dfshealth.html"

Big Data? Big vulnerabilities!
With such a query with concatenation, we get the search results with a list of vulnerable systems based on Hadoop. You can browse the HDFS file system directly from your browser and download any file.
Google Dorks is a powerful tool for any pentester that not only an information security specialist, but also an ordinary network user should know about.
Thank you all for your attention!
Comments
Post a Comment