
Work of Fluxion:
- Scan for a target wireless network.
- Launch the Handshake Snooper attack.
- Capture a handshake (necessary for password verification).
- Launch Captive Portal attack.
- Spawns a rogue (fake) AP, imitating the original access point.
- Spawns a DNS server, redirecting all requests to the attacker’s host running the captive portal.
- Spawns a web server, serving the captive portal which prompts users for their WPA/WPA2 key.
- Spawns a jammer, de-authenticating all clients from original AP and luring them to the rogue AP.
- All authentication attempts at the captive portal are checked against the handshake file captured earlier.
- The attack will automatically terminate once a correct key has been submitted.
- The key will be logged and clients will be allowed to reconnect to the target access point.
Installation
Installation process of fluxion in our Kali Linux is quite easy and simple. As the many other tools we also need to clone fluxion from it'd GitHub repository.
To clone it we use following command in our Kali Linux terminal:
git clone https://github.com/FluxionNetwork/fluxion
This command will clone the fluxion in our system.
Now we navigate to fluxion by using simple cd command:
cd fluxion
Now for the first time we run the bash script called fluxion.sh with -i flag to install the requirements to use fluxion:
sudo ./fluxion.sh -i
From the next time we don't need to use the -i flag, we just run:
sudo ./fluxion.sh
In the following screenshot we can see that we are installing our missing packages:
After installing requirements it will start automatically and prompts for choosing language:
Then we need to select the wireless interface. If our system's wireless interface supports packet injection and monitor mode then we can go with it. But our Laptop's wireless chipset does not support injection and monitor mode so we use a Alfa wireless adapter AWUS036NEH (Available on Amazon, all the external wireless adapter in market does not supports monitor mode & packet injection).
Then we need to search for WiFi networks around us:
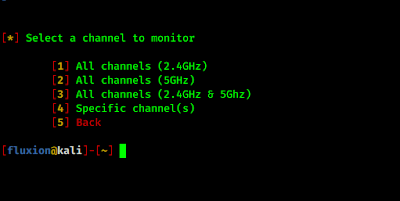
We can search dual band or any specific channel signals here.
Then it will start searching wireless networks nearby us.
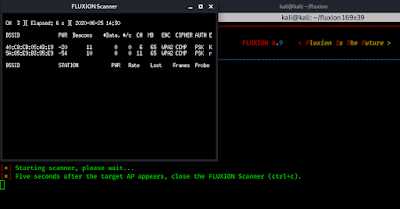
We give it some time to detect all networks then we stop it we press ctrl+x, and it will show us the founded WiFi networks.
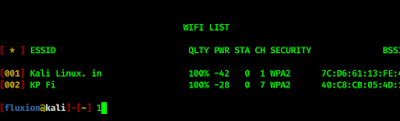
Now we select the wireless interface for tracking (If we are not sure what to do then we can skip this by selecting option 3).
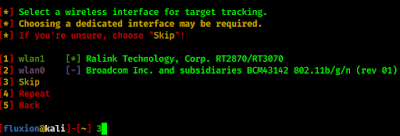
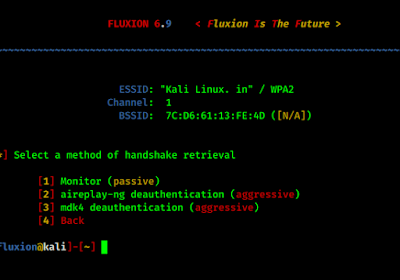
Then we need to choose handshake retrieval method:
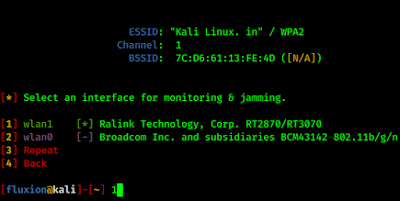
For jamming and monitoring we must need to select interface (in our case we need to select our Alfa card i.e wlan1)
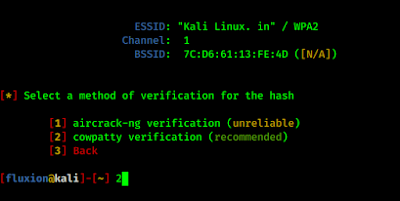
Now fluxion prompts for verification hash process we go with the recommended.
Rest all the options are basics and nothing much to tell about it. Fluxion will de-authenticate all the target connected with our targeted wireless network. When the de-authenticated devices try again to connects fluxion will capture the handshake.
We can do this type of things also in aircrack-ng but fluxion is advanced and user-friendly.
Fluxion is also capable to perform a Evil-Twin attack. In this attack technique we send de-authentication packets continuously to the target that all the client of target device will got disconnect and that time we create another WiFi with the same name and if clients thinks your WiFi as their original they got trapped and we got their credentials. Almost like phishing.
This comment has been removed by a blog administrator.
ReplyDelete