
Threat actors breaching company networks are deploying a cornucopia of malware over the remote desktop protocol (RDP), without leaving a trace on target hosts.
Cryptocurrency miners, info-stealers, and ransomware are executed in RAM using a remote connection, which also serves for exfiltrating useful information from compromised machines.
Exploiting Windows RDS features
The attackers leveraged a feature in Windows Remote Desktop Services that allows a client to share local drives to a Terminal Server with read and write permissions.
These drives appear on the server as a share on a virtual network location called 'tsclient' followed by the letter of the drive and can be mapped locally.
The feature has been around for a long time, and properly explained what happens when a user connects to the server and runs an application.
Access to the resources shared this way is possible through RDP and no trace is left on the client machine's disk as applications execute in memory. When an RDP session terminates, so do associated processes and memory is typically released.
Malware cocktail in network shares
Malware analysts at Bitdefender found that adversaries take advantage of this feature and drop multiple malware of various types along with a component named 'worker.exe' that receives instructions from the attacker.
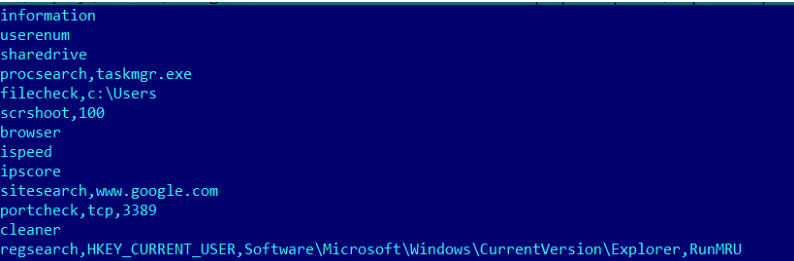
In use since at least February 2018, 'worker.exe' is an off-the-shelf tool used by multiple threat actors, especially for its reconnaissance capabilities.
Among the details this component can collect from a system are the following:
System information: architecture, CPU model, number of cores, RAM size, Windows version
domain name, privileges of the logged user, list of users on the machine
local IP address, upload and download speed, public IP information as returned by the from ip-score.com service
default browser, status of specific ports on the host, checking for running servers and listening on their port, specific entries in the DNS cache (mainly if it tried to connect to a certain domain)
checking if certain processes are running, existence of specific keys and values in the registry
These features are complemented by the ability to take screenshots and to enumerate all connected network shares that are mapped locally.
Apart from this, 'worker.exe' was seen executing at least three separate clipboard stealers (MicroClip, DelphiStealer, and IntelRapid), two ransomware families (Rapid and rapid 2.0, and nemty), multiple Monero cryptocurrency miners (all based on XMRig), and, since July 2018, the infamous AZORult info-stealer.
Samples of 'worker.exe' were found in a 'tsclient' network share and noticed that they did not connect to a command and control (C2) server for instructions. Instead, it took commands from a text file named 'config.ins' in the same location.
All information collected from the host goes into a .NFO file that is stored in the same location as the configuration file.
This is a convenient way to keep the data off the compromised computer and make the forensic analysis more difficult.
A pretty penny
The purpose of all three clipboard stealers is to determine when the user copies a cryptocurrency wallet address and replace it with one belonging to the attacker.
This way, any outgoing transaction will miss its intended destination and find its way into the cybercriminal's pockets.
Of these three pieces of malware, IntelRapid is more advanced. It can recognize a much larger number of cryptocurrency wallets (Bitcoin, Litecoin, Ethereum, Monero, Bitcoin Cash, Dash, Ripple, Dogecoin, Neo, and ZCash) and replaces them with similar alternatives provided by the attacker.
Using a "complex scoring mechanism," the malware picks replacements that begin or end with the same characters as the victim's address. This is most likely to fool users that are more attentive to the pasted wallet address.
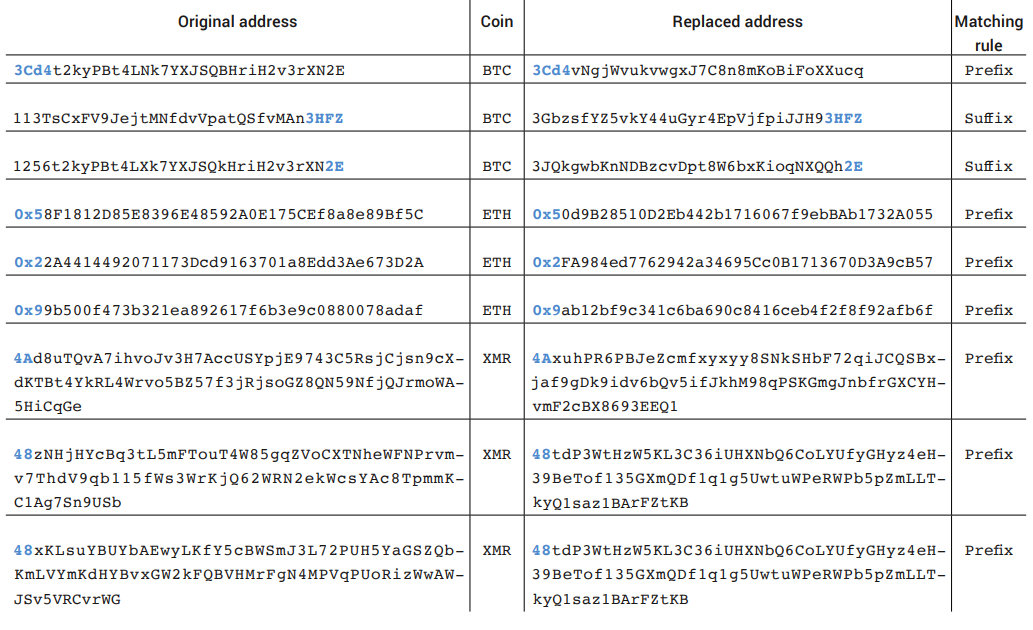 Wallet address replacements starting/endign as the original
Wallet address replacements starting/endign as the original
Depending on the cryptocurrency, IntelRapid could check in excess of 1,300 addresses to find strings that are similar to the original one from the victim.
From analyzing the replacement addresses, Bitdefender determined that the clipboard stealers were deployed by the same threat actor.
Further investigation into other malicious components indicated a connection with the ransomware families, the cryptocurrency miners, and the AZORult info-stealer sample they analyzed.
The earnings from the clipboard stealers, based on transactions for replacement addresses in a main cluster, amounted to $150,000. The real profit is likely much larger, though, since Monero was not included.
On the same note, other revenue streams have also been left out since they could not be estimated, such as money generated by the cryptocurrency miners or from the ransomware payloads.
Original point of compromise
From their findings, the researchers could not work out how the attacker gained access to the network in the first place or how they managed to plant 'worker.exe' on the 'tsclient' share.
Also a mystery is how the adversary got valid RDP credentials to access a victim host; bruteforcing being is one possibility.
It is important to note that professional network intruders that break into the digital perimeter of a company often advertise their access on underground forums.
Cybercriminals interested in any of the targets can pay between a few hundred USD to thousands and more for access, or to have their malware dropped.
This is a typical scenario for ransomware affiliates who many times partner with such access-as-a-service providers to get to large targets that can be asked to pay a higher ransom to have their files decrypted.
Victims across the world
The campaigns observed by Bitdefender are likely not discriminating between the targets that can be compromised. This indicates cybercriminal in the money-making game.
"From our telemetry, these campaigns do not seem to target specific industries, instead trying to reach as many victims as possible" - Bitdefender
Most of the victims are in Brazil, the U.S., and in Romania, the researchers note in a report this week.
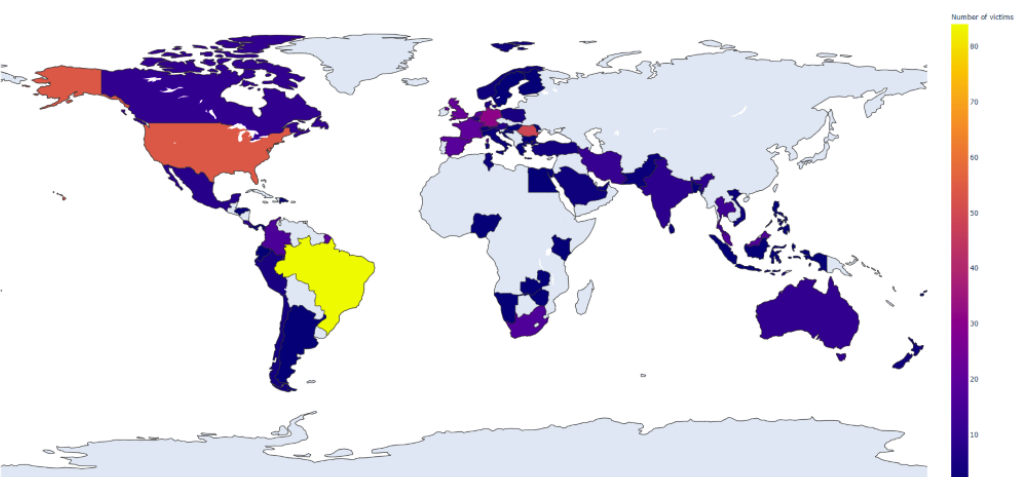
As visible from the spread of the victims across the globe, the attacker is not interested in certain victims but cares more if they come in great numbers.
Preventing this type of attack is not difficult and can be done by disabling drive redirection from the list of group policies. The option is available by following this path in the computer configuration applet:
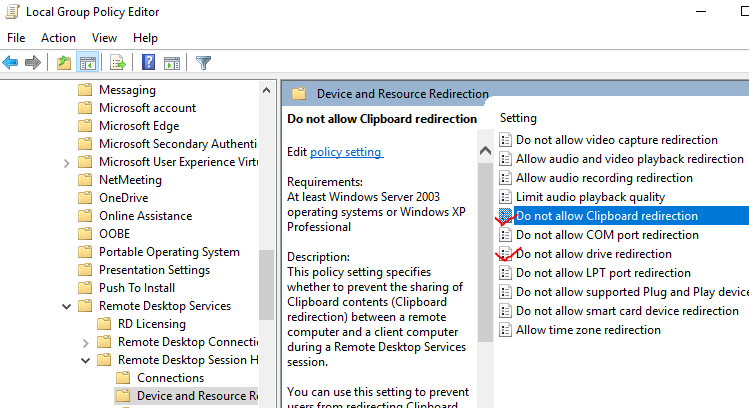
Below is the full path:
Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Device and Resource Redirection
Comments
Post a Comment